Google has decided to remove ads that use to show up on the right hand side of desktop browser windows. Instead they have opted to show ads at the top of the search results page and limit the number of ads to four results and then display the top organic search results below. This will definately impact companies with smaller AdWords budgets and directly affect the the click through rates and overall ROI for these companies. If you have a smaller advertising budget than your competitors and plan on staying competative with the same budget it might be time to think about moving some of your marketing money to social media.
MORE INFO
What Is PII?
 PII is an acronym for Personally Identifiable Information and stealing it is the goal of most cyber attacks. It is information about yourself to keep private at all times; your name, date of birth, mother’s maiden name, Social Security Number, address, phone number, account numbers, and e-mail address. Attackers want to use your PII to create or take over accounts in your name.
PII is an acronym for Personally Identifiable Information and stealing it is the goal of most cyber attacks. It is information about yourself to keep private at all times; your name, date of birth, mother’s maiden name, Social Security Number, address, phone number, account numbers, and e-mail address. Attackers want to use your PII to create or take over accounts in your name.
HAPPY HABBIT 1: Never share your PII. Don’t give out your name, date of birth, mother’s maiden name, Social Security Number, address, phone number, account numbers, and e-mail address.
We most commonly protect computer accounts with a combination of Usernames and Passwords. A Username is usually a version of your name or a nickname to use for computer accounts that uniquely identifies you to the system you want to access (example: m_ryczek). A Password authenticates to the computer system that you are the user you say you are.
Complex Passwords Made Simple
A complex password contains a mix of upper and lower case letters (AaBbCc), numbers (123456), and special symbols (!@#$%^).
Create passwords eight or more characters in length.
Do not use words found in the dictionary.
Do not use names.
Make it difficult for other people to guess.
These rules seem excessive. Complex passwords are hard to remember, but it’s not the password you should try to memorize. Since ideas are easier to remember than codes, you should memorize your method for making the password, instead. Consider the following example:
Choose a musician and a line from a song they wrote. Then extract a single letter from each word in their name and the song lyric, mix in the date, and add some special characters.
Example: Tom Petty and the Heartbreakers: “into the great wide open a rebel without a clue” becomes: TPatHitgwoarwac.
Next, modify today’s date (05/14) using special characters by holding shift when typing the numbers: 05!$.
Finally, add on some characters from the place you’re logging into. For example, a Youtube password could have the characters YT at the end, and for Yahoo, add YH at the end, and so on. By adding this step to your password making process, you are automatically making a different password for each place you login.
The resulting password looks like: TPatHitgwoarwac05!$YT
You will want to scramble the rules given in the previous example. Make them your own and keep them to yourself. Change your passwords often. Don’t let them get over 90 days old.
HAPPY HABIT 2: Only use complex passwords.
HAPPY HABIT 3: Never give anyone your password.
Forgotten Password Recovery Questions
Everyone forgets passwords. Most logon screens offer an option to recover or reset your password after you answer a set of recovery questions. Understand that the recovery answer you use doesn’t have to actually answer the question. Also, the recovery questions don’t recognize the difference between upper and lower case letters.
For example: “What is your hometown?” could be answered with “coloradoavalanche” or “ColoradoAvalanche.”
Forgotten Recovery Questions
Choose three answers that you’ll only use for password recovery. Make sure your answers don’t have anything to do with the real answer. Avoid using spaces in your answers. Keep these answers private. Make a habit of changing recovery answers from time to time.
Social Engineering and How to Protect Yourself
Why would a computer attacker try to crack your password when it’s much easier to trick you into giving it to them? That’s what social engineering is. Cyber attackers lurk all over the Internet. But when they’re not online, they’re glancing over your shoulder while you check your email in a public place. They’ll scrounge through dumpsters looking for anything they can use to get more information. They have a trick for every situation and location.
Offline Security
HAPPY HABBIT 4: Shred papers and crack old discs into pieces containing PII before you throw them away.
Online Security
Be suspicious of everything. The anonymity of the Internet allows attackers to impersonate anyone.
If you don’t see a lock on your browser, you are vulnerable to eavesdropping.
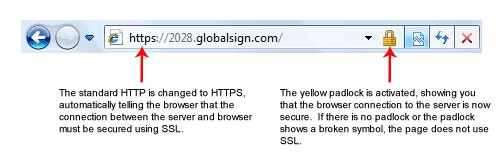
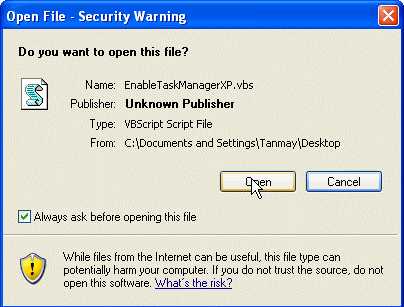 HAPPY HABIT 5: Read warnings before clicking “Ok.” Unless it was something you specifically wanted, assume it’s going to load malicious software onto your computer or direct you to a malicious website.
HAPPY HABIT 5: Read warnings before clicking “Ok.” Unless it was something you specifically wanted, assume it’s going to load malicious software onto your computer or direct you to a malicious website.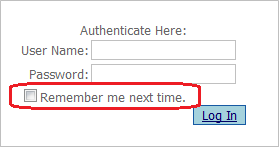
HAPPY HABIT 6: Never use “Remember Me” checkboxes for logging in to websites. Remember to use complex passwords.
HAPPY HABIT 7: Always end the session by logging out of a website. This will protect from anyone reusing that session.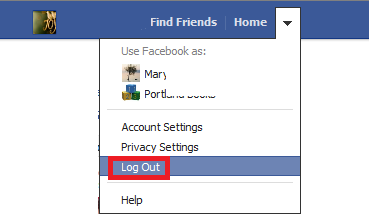 It’s the same as saying goodbye to end a phone conversation. Both parties know that communication has ended.
It’s the same as saying goodbye to end a phone conversation. Both parties know that communication has ended.
HAPPY HABIT 8: Be aware of the web address you’re using. If the address says anything unusual or something unrelated to what you’re connecting to, don’t trust that website. http://www.google.com should always take you to Google.
HAPPY HABIT 9: If you don’t want someone to see it, don’t put it online. Once you hit “enter,” it’s on the Internet forever.
Email Security
HAPPY HABIT 10: Use your spam filters. Identifying spam thwarts would-be attackers, but also allows more bandwidth for things we want.
HAPPY HABIT 11: Never click a link in an untrusted email. If it seems like a scam, it is.
HAPPY HABIT 12: Never click “Unsubscribe” links in junk email. Mark it as spam and move on with your life.
HAPPY HABIT 13: Always make a backup copy of data you want to keep. Store the original on your hard drive and store the backup copy on removable storage media like DVDs, CDs, or USB drives. Although these are easily lost or stolen, your original file is still stored on your hard drive; and vice versa. If your hard drive fails, or your computer is stolen, you still have a duplicate of your data.
HAPPY HABIT 14: Use a physical lock. It’s the same as a bike lock but it’s for computers. Remember it only takes a second to steal an unattended laptop.
HAPPY HABIT 15: Use the screen lock function on desktops, laptops, phones and tablets; in case you and your devices become separated.
contact us
Office phone: (303) 868-4928
Address: 2224 S Fraser St. Unit 5 Aurora, CO 80014
Hours: 9am-5pm MT Monday to Friday